The Industrial Internet of Things (IIoT) is transforming the manufacturing industry by enabling real-time monitoring, control, and optimization of industrial processes. However, with the growing number of interconnected devices, the risk of cyber attacks on IIoT systems is also increasing. Therefore, it is essential to implement robust cybersecurity measures to protect IIoT systems from potential threats.
DDoS and ramsonware attackers are exploiting vulnerabilities at breakneck speed
20 Jun, 2022
Hertzbleed hacks target computer chips to steal sensitive data

7 Jun, 2021
Colonial Pipeline Paid Roughly $5 million in ramsom to hackers
20 May, 2022
Fears grows for smaller nations after ransomware attack on Costa Rica escalates

2 Jun, 2022
Foxconn confirms ransomware attack disrupted operations at Mexico factory

29 May, 2022
Ransomware attack sends US county back to 1977
16 Jun, 2022
Largest HTTPS DDoS Attack on Record - 26m request per sec

~IIoT Cyber Security~
IIoT is Sweeping The World
The increasing use of IIoT systems in manufacturing operations makes it essential to prioritize cybersecurity. By implementing robust cybersecurity measures and regularly assessing and updating them, businesses can mitigate the risk of cyber attacks on their IIoT systems, reduce downtime and equipment damage, and protect their employees and reputation.
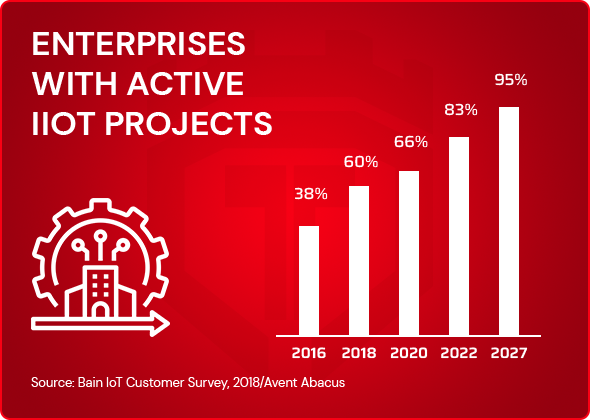
80%+ Industrial enterprises would implement IIoT projects by 2022
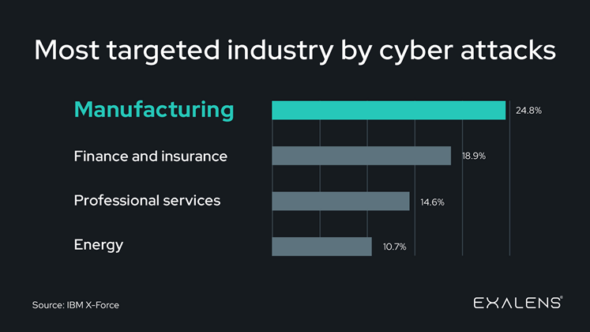

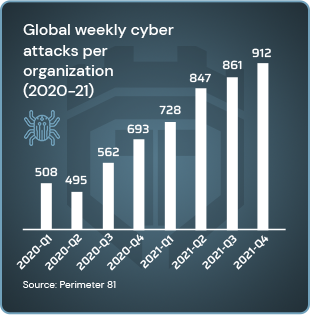
IIOT attack target potential increase year after year
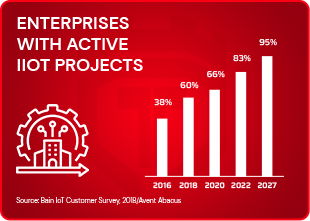
IIoT Cyber Security
IIoT Vulnerability Linked Attacks Are Now Overdue
A growing concern as the adoption of IIoT devices and systems continues to rise. Industrial systems have traditionally been isolated from the internet, making them less vulnerable to cyber threats. However, as IIoT devices become more common, they are increasingly connected to corporate networks and the internet, which makes them more vulnerable to cyber attacks.
More than 1/2 the organizations with IIoT devices have no security measures in place
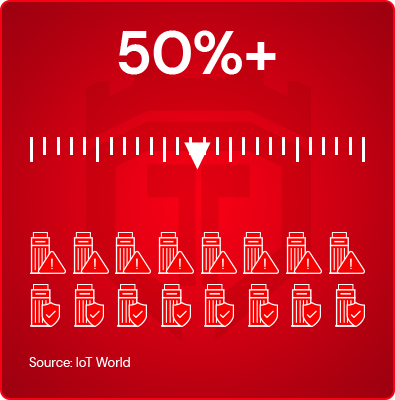
Number of Cyber Security incidents increased by 50% in just one year
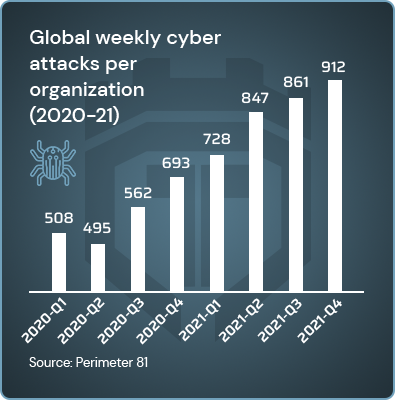
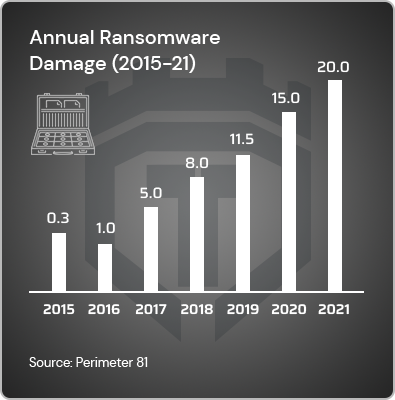
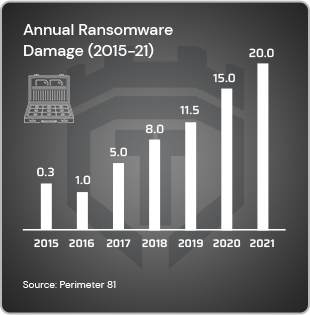
In 7 years ransomware damages leapfrogged 61x
~Our Approach~
Anomaly Detection for IIoT Devices
Advanced ML Model
A sophisticated machine learning algorithm designed to analyze complex data patterns and make accurate predictions or decisions.
Real Time Monitoring
The continuous observation and analysis of data as it is generated.
Immediate Anomaly Notification
Instant alerts triggered by the detection of unusual or abnormal data patterns.
Root Cause Analysis
A methodical process used to identify the underlying reasons for an anomaly, allowing for immediate insights and actions.

