~Cybersecurity at the Source, Using AI to Ensure Protection~
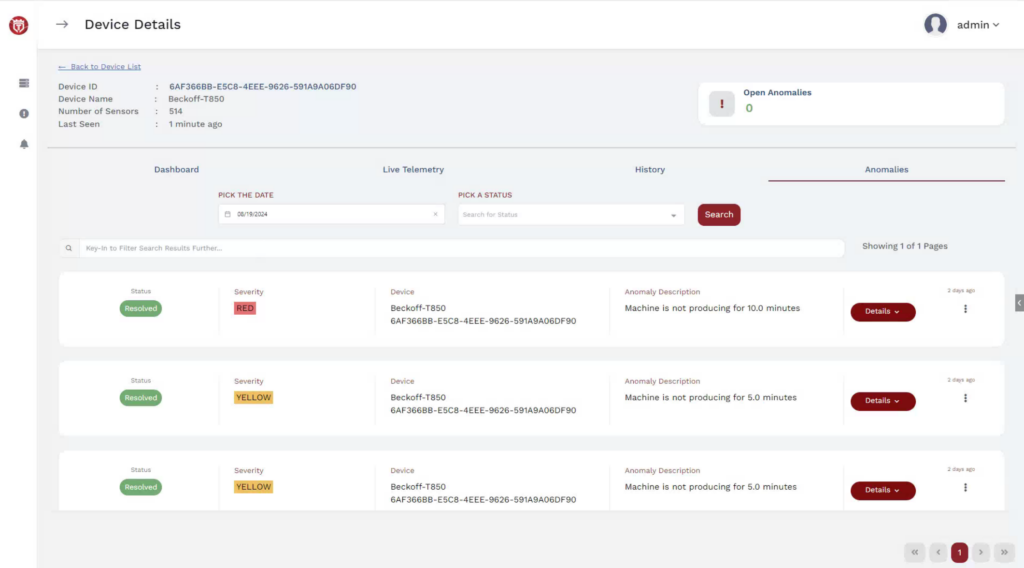
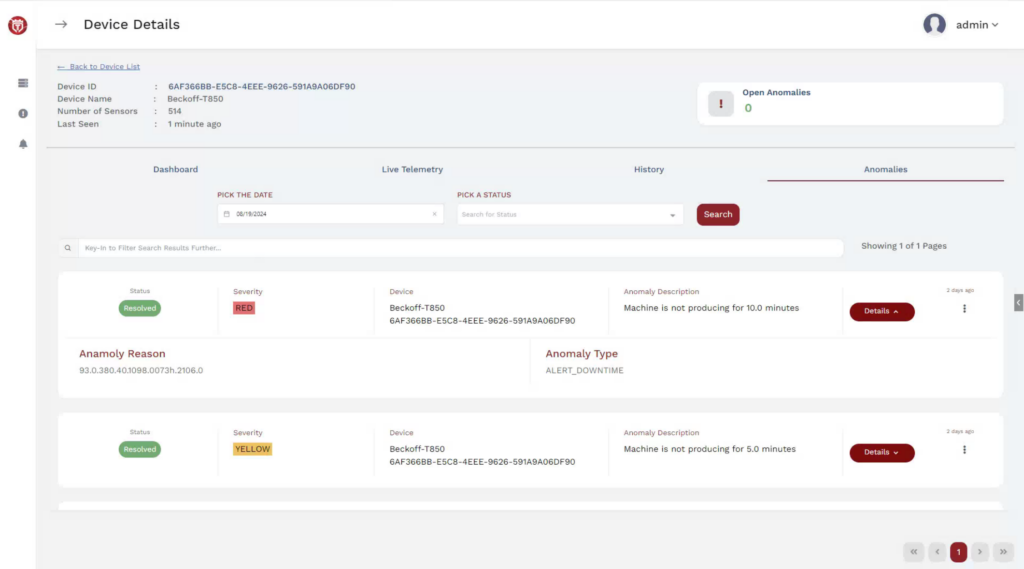
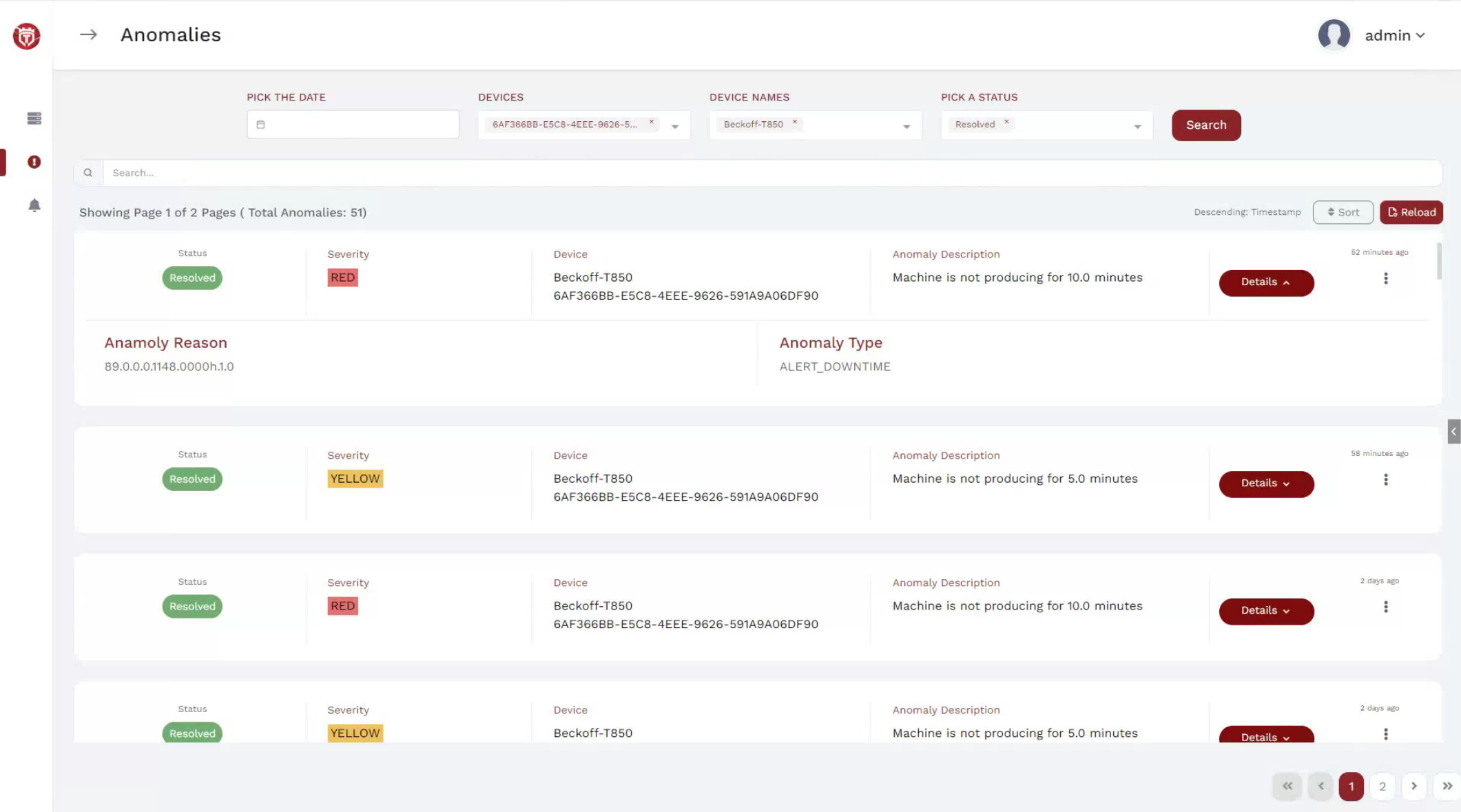
Trustcore is addressing operational technology (OT) cyber security, machine failure, alarms, and preventative maintenance. Trustcore BA identifies and diagnoses cyber-attacks as well as industrial machine malfunctions through the use of machine learning technology. Trustcore BA reports the anomalies to the manager along with the root cause analysis, enabling quick recovery and reduced downtime. All anomalies and related data are easily accessible through the management user interface with the ability to further drill down and run reports. The enhanced machine learning and real time monitoring contributes to factory efficiency, productivity, reduced costs, and improved product quality.
Industry 4.0 connects the IT and OT networks. Hackers now have more opportunity with the increased connected endpoints. In addition, the lack of analytics and real time monitoring of factory machines causes quality issues in output as well as reduced productivity. Having to address several machine alarms with little to no information for troubleshooting, leads to increased downtime. Factories may require to shut down or suffer financial losses due to an undetected cyberattack or machine malfunction. The intelligence of Trustcore BA addresses the issues of security and overall operational efficiency that factories face in the industry.


TrustcoreBA
- On-board containerized application
- Anomaly detection using BA and AI
- Zero Trust Architecture
- DDOS and Ransomware protection
- Preventative maintenance and repair

Why OT Must Be Protected with AI at the Source?
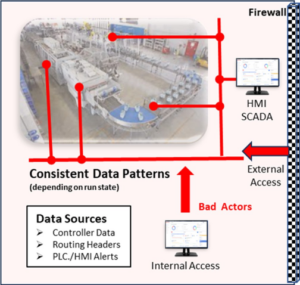
At Trustcore, we believe that the use of artificial intelligence is the only way to compete with the ever- changing landscape of cyber-attacks and the infrastructure management of Industry 4.0.
Industry 4.0 is focused on connecting the operation technology (OT) network to the information network so that the information connected from the digitized Industrial Control Systems (ICS) can be used to enhance efficiency, reduce costs, and improve product quality. The problem faced is that cyber hackers can now enter the IT network through the ICS devices, as well as the ICS devices can be accessed through the IT network. In addition, the digitization of the ICS devices needs to be leveraged to be able to quickly recover from failures as well as automate the preventative maintenance, and repair (PMR) function.
Trustcore BA consistently monitors your data sources and learns their run and non-run consistent patterns using a series of artificial intelligent techniques that detects various control packet, network traffic, and alert variations to not only notify you, but takes action to limit production losses by detecting, preventing, and identifying the root cause of the anomalous behavior.